Overview :
In this article, we will explore how to protect an API in API Gateway using JWT. API Gateway can function as a JWT issuer and will leverage that capability to secure the API we created in the previous article. If you haven’t checked that out yet, please click here. In the upcoming articles, we will explore configuring an external JWT issuer as well.
Prerequisite :
- Should have API Gateway administrator access.
- Basic knowledge of API Gateway.
- Basic idea of JWT.
Configure Local JWT in API Gateway :
- Login to API Gateway and click on the ‘Administration’ button.

- Click on ‘Security‘ and then select ‘JWT/OAuth/OpenID‘ You will be able to see both the ‘Local Authorization Server‘ and the ‘External Authorization Server‘ We will update the local server to function as a JWT Issuer.
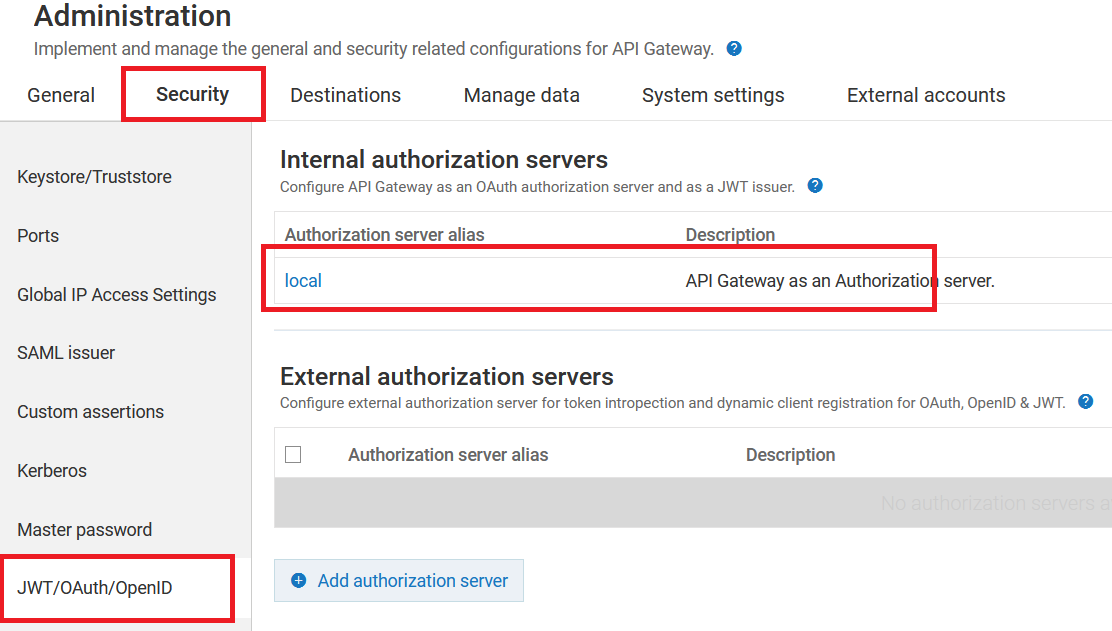
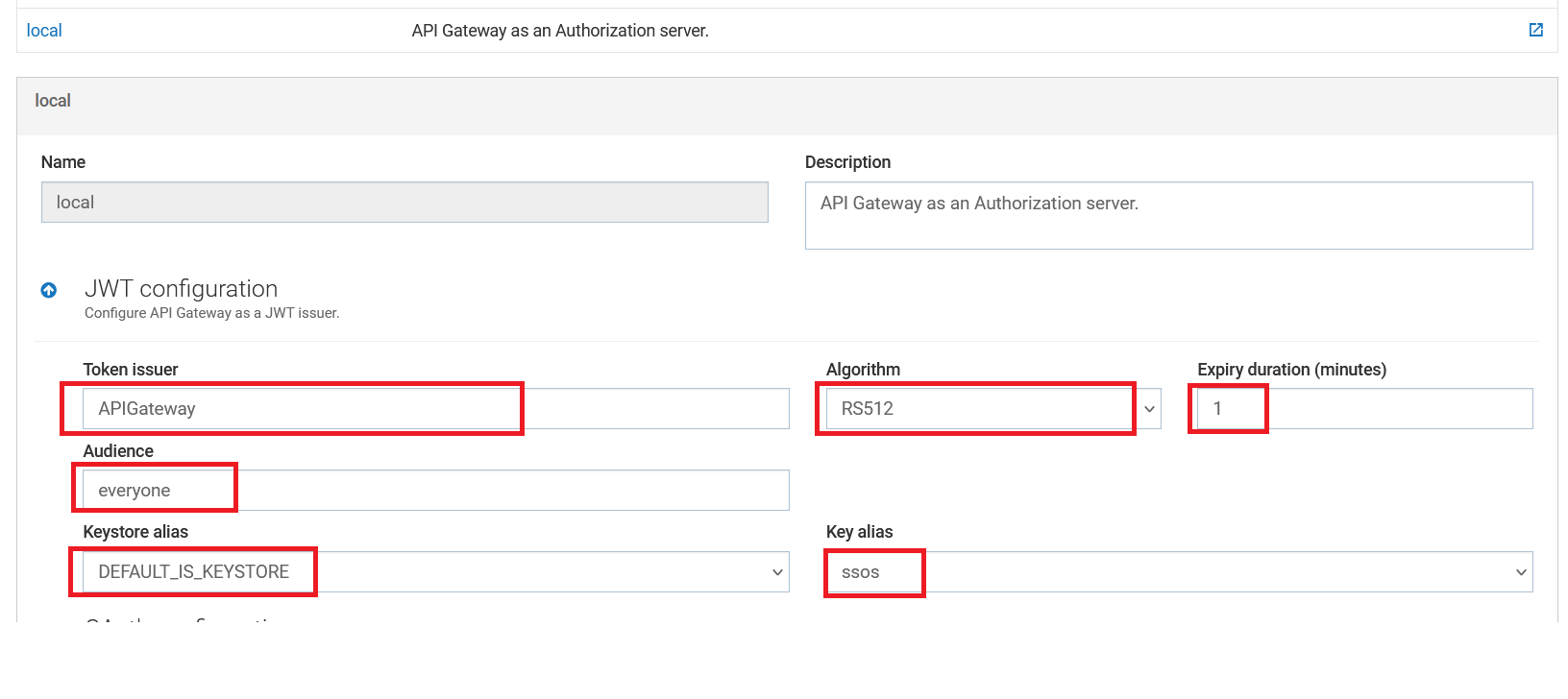
- Update the local server JWT information with the provided values. You can also modify these values. If desired, you may choose an alternative algorithm. For the keystore and key alias, select the default options.
Configure Application in API Gateway :
An application in API Gateway provides specific identification criteria, such as HTTP headers or IP address ranges. This information is crucial for the API Gateway to authenticate and recognize incoming messages from distinct applications during runtime. By defining precise identifiers, the API Gateway ensures secure and controlled access, allowing only authenticated applications to interact with the associated APIs.
- On the API Gateway home page, click on ‘Applications‘ in the navigation bar. This action will open the ‘Applications‘ page. Once on the ‘Applications‘ page, click on the ‘Create Application‘ button.
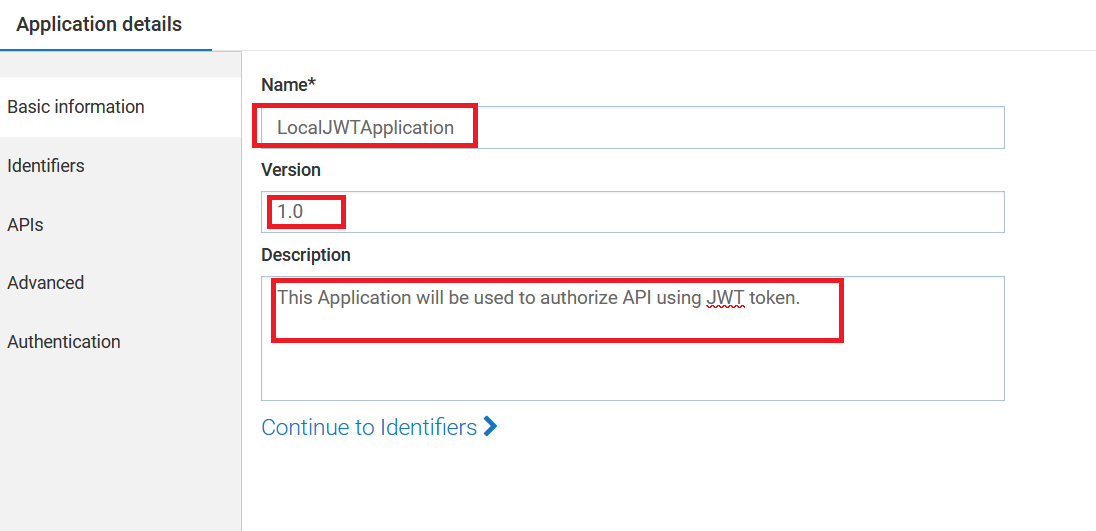
- In the Basic Information tab, fill in the application name, and version, and provide a description.
- Navigate to the ‘APIs‘ tab, and select the PetStore API using the search button. You can also add multiple APIs to a single application.

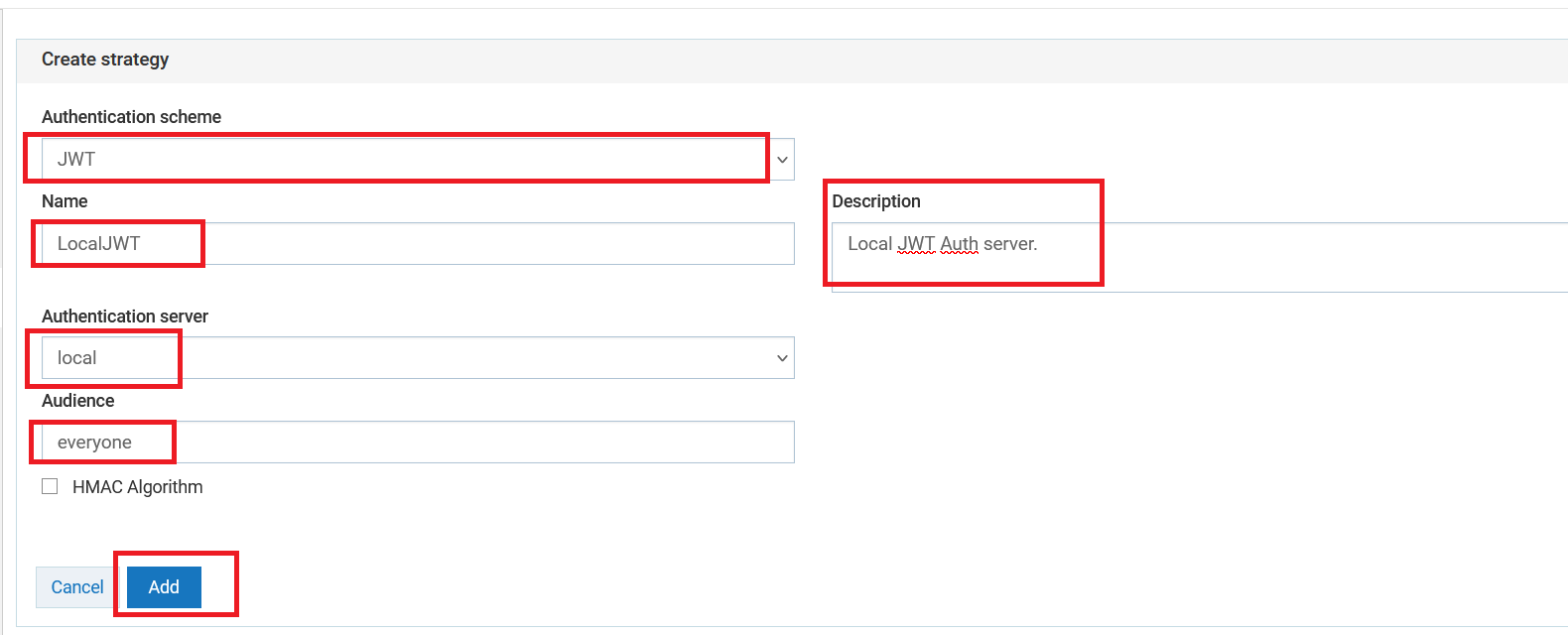
- Navigate to ‘Authentication‘ and click on the ‘Create Strategy‘ button.
- Select ‘JWT‘ as the authentication scheme, set the authentication server to ‘local,’ and fill in the other details as shown in the screenshot below.
- After filling in those details, click on ‘Add‘ and make sure to enable it. You can do this on the Application page by using the toggle button.
Protect API Using JWT token :
- Open the PetStore API and edit it.
- Navigate to the ‘Policy‘ section and insert the ‘Identity & Authorize‘ policy, which can be found under ‘Identity & Access‘.
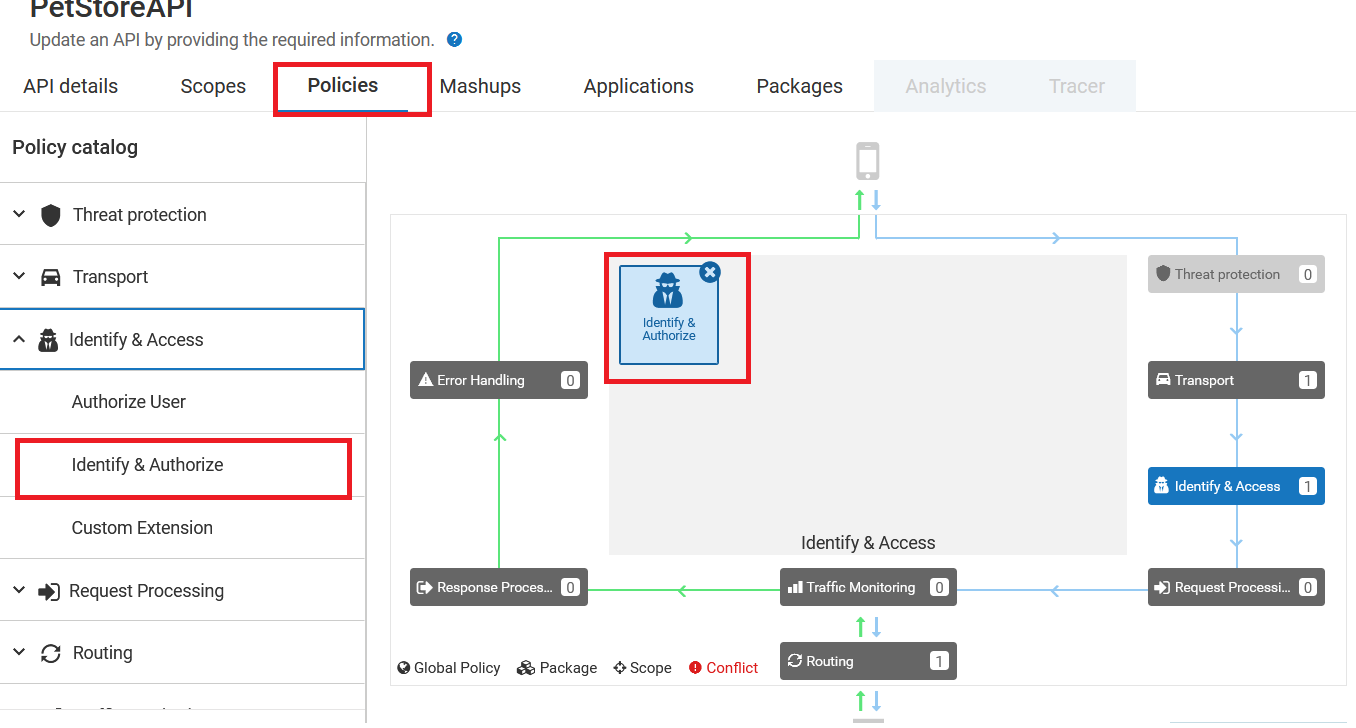
- In the ‘Policy Properties‘ choose ‘JWT‘ and configure the Application Lookup condition to ‘Register Application‘ as we have already registered the application with our API.
- Once you configure it save the API.
- Now if you call the API using Postman without using JWT then you will get the below error from API Gateway.
{ "Exception": "API Gateway encountered an error. Error Message: Unauthorized application request. Request Details: Service - PetStoreAPI, Operation - /pet/{petId}, Invocation Time:3:18:10 PM, Date:Jan 20, 2024, Client IP - ***.**.*.*, User - Default and Application:sys:defaultApplication" }
Generate JWT Token and call API :
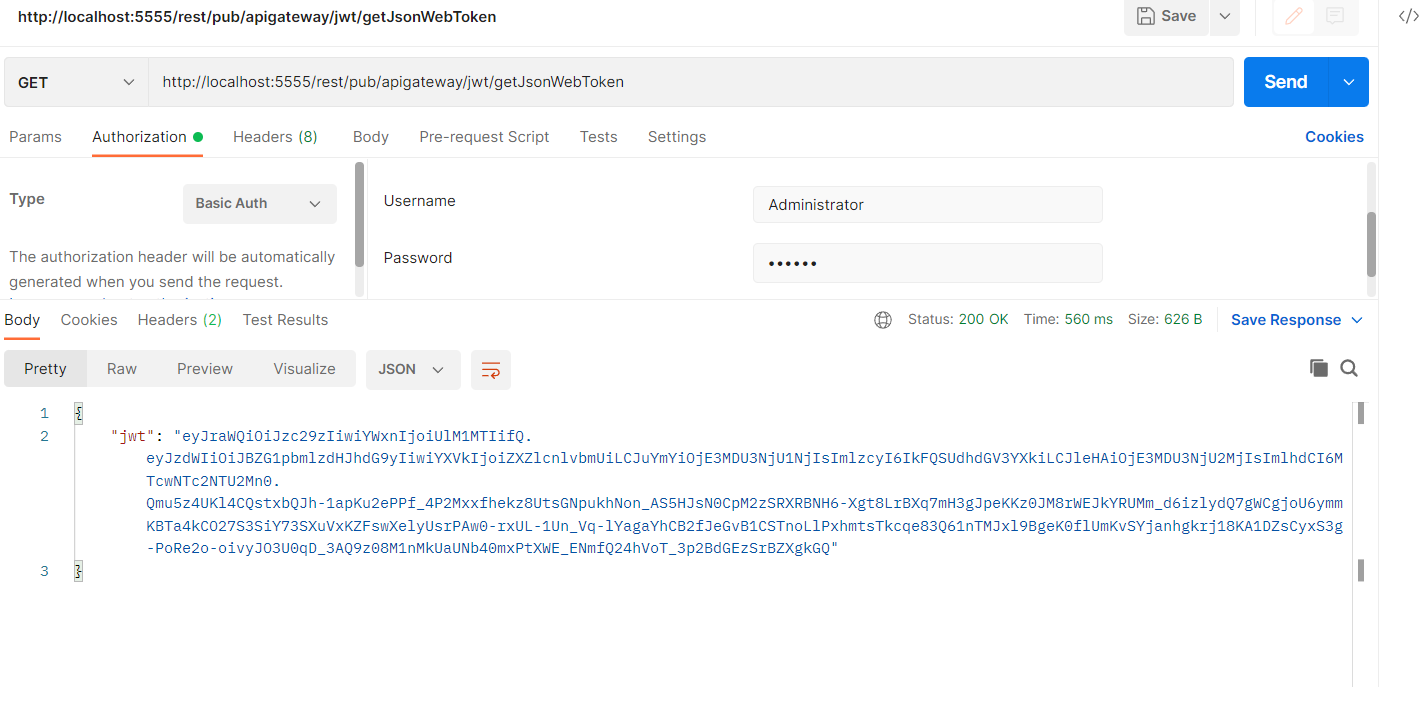
- Call the below URL to generate the JWT token and the same can be used to call the PetSTore API.
Ex: http://host:port/rest/pub/apigateway/jwt/getJsonWebToken - After making a call to the specified URL, you will encounter an error. To resolve this issue, set pg_JWT_isHTTPS to false in order to make it functional.
{ "errorDetails": " Transport protocol must be HTTPS." } - Navigate to ‘Extended settings‘ using ->Administration -> General -> Extended settings.
- Find pg_JWT_isHTTPS setting and set it to false.
Note: The above steps are only required if you have done on-premise API Gateway installation. - Now if you hit the able URL again, you will get the JWT token.
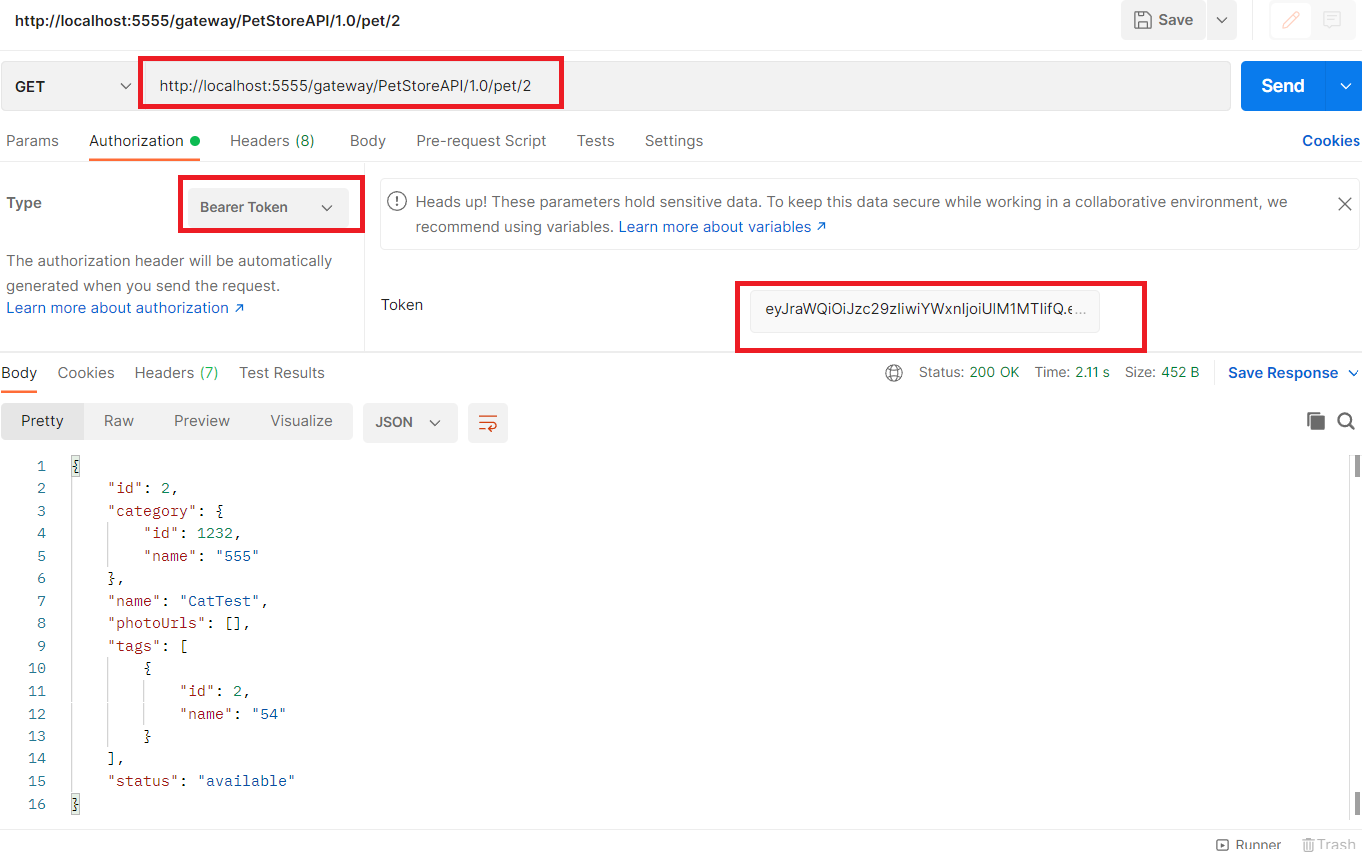
- Call the Petstore API using the API Gateway endpoint and include the JWT token as the bearer token in the request. You should then observe the results.
I hope you found this article both informative and useful, Cheers!

This article offers a fascinating perspective on the subject. The depth of research and clarity in presentation make it a valuable read for anyone interested in this topic. It’s refreshing to see such well-articulated insights that not only inform but also provoke thoughtful discussion. I particularly appreciated the way the author connected various aspects to provide a comprehensive understanding. It’s clear that a lot of effort went into compiling this piece, and it certainly pays off. Looking forward to reading more from this author and hearing other readers’ thoughts. Keep up the excellent work!
Great article! The clarity and depth of your explanation are commendable.